Comprehensive XSS
9 sections
16 challenges
Master cross-site scripting (XSS). Practice your skills with simulated XSS-vulnerable labs of increasing complexity and fun. Exploit real vulnerable software with just enough guidance.
We will dive into persistent and reflective XSS: how to exploit them and how to prevent them. While investigating real-world vulnerabilities, we’ll also examine source code to help determine the root cause.
Ready to start?
Ready to start?
Labs
Combine XSS & social engineering to “help” other players
Exploit persistent XSS for some in-game currency
Real software vulns
Steal cookies from a learning platform
Find & exploit a vuln in a Git service
What’s inside?
Introduction
We address burning questions about XSS (“is it even relevant today?”) and strip it down to its core to show you what the absolute simplest XSS vulnerability looks like.
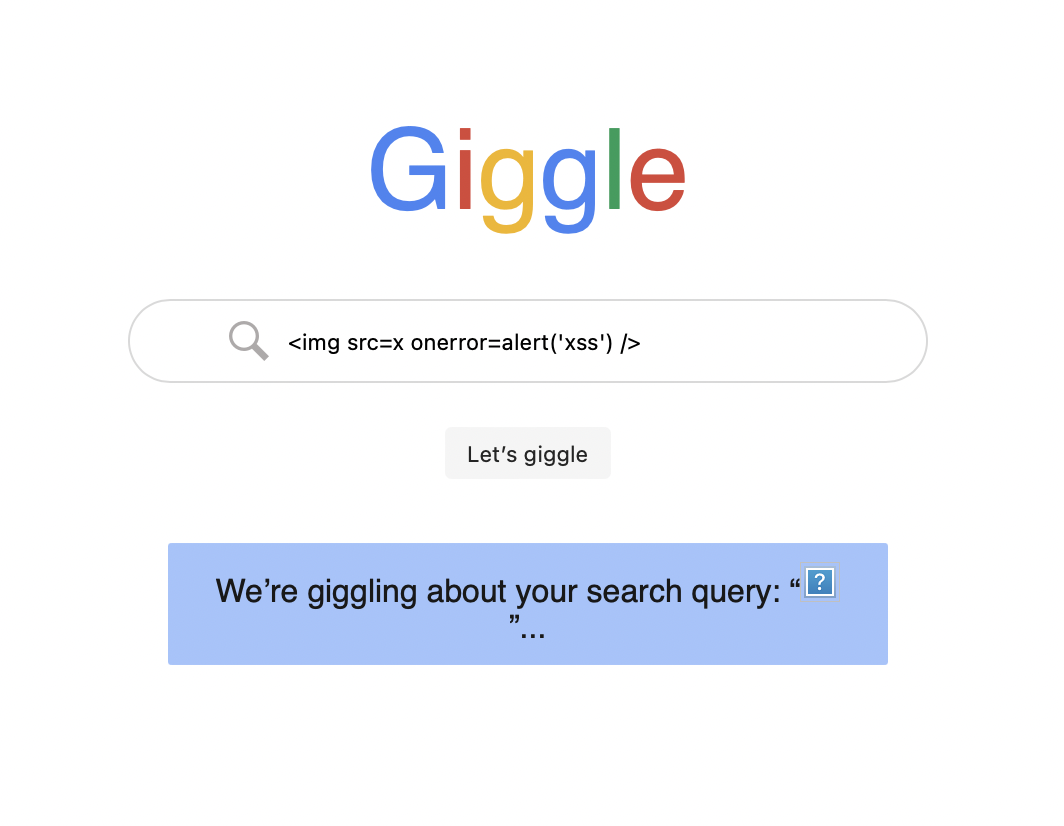
Reflected XSS: Real-World Case Study
You’ll exploit the first real-world vulnerability of this course — a reflected XSS vulnerability in Moodle version 3.10.0 to steal a cookie! We also look at the vulnerable source code and the patch that finally fixes this vulnerability.
Reflected XSS: Practice
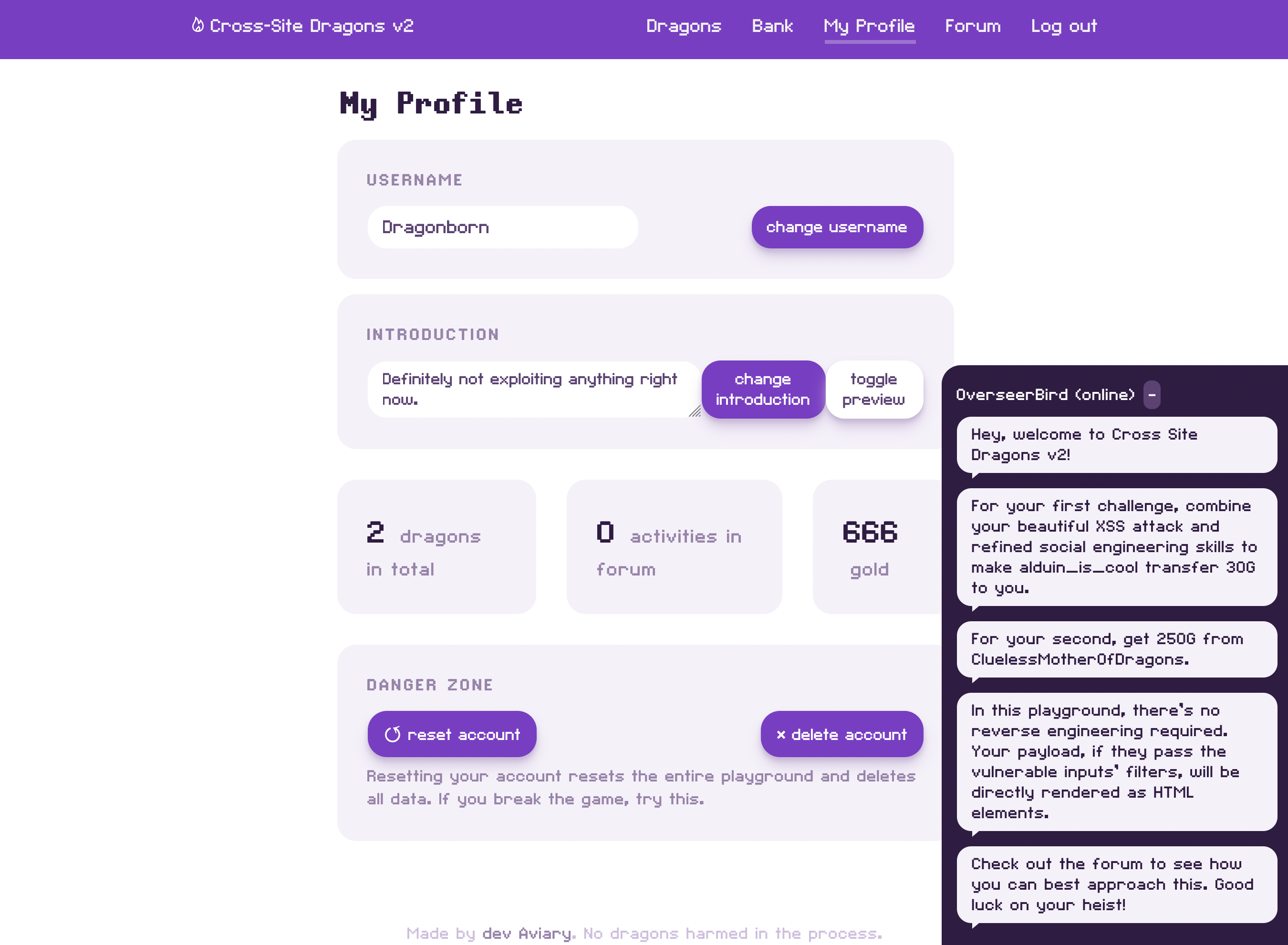
Attackers achieve the greatest impact with XSS attacks when they’re combined with carefully crafted social engineering tactics, due to XSS attacks being client-side.
Introducing... Cross-Site Dragons, a browser game where you wield your XSS power fortified with some social engineering to log out unsuspecting users and delete their accounts!
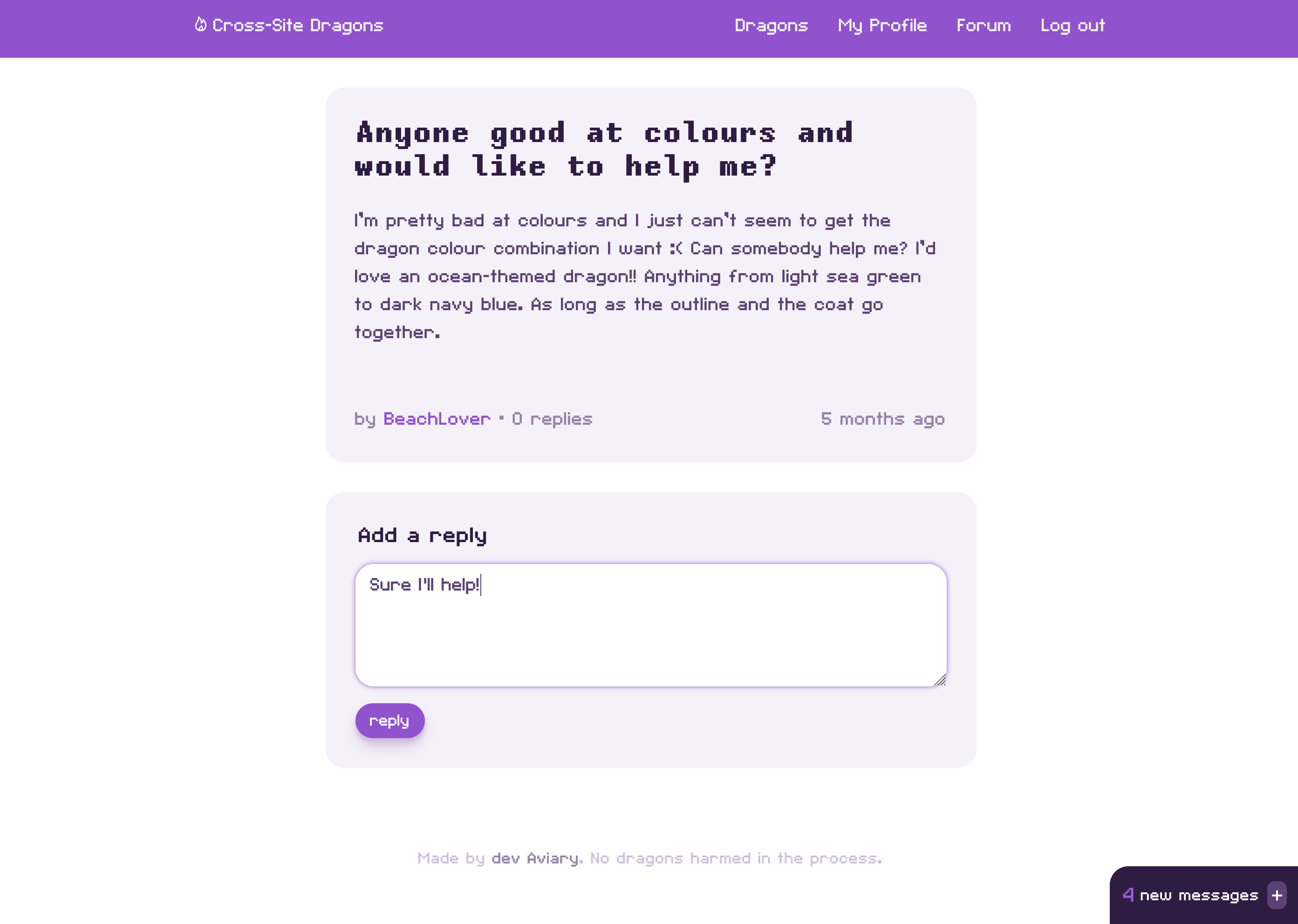
Persistent XSS: Introduction
What happens when your XSS attacks are persisted, and thus amplified without you having to put in the extra effort?
We examine the simplest persistent XSS vulnerability in a faux-Twitter lab.
Persistent XSS: Real-World Case Study
In this real-world case study of the persistent XSS vulnerability in Gitea version 1.12.0, you are now tasked with finding the vulnerability and creating your own Proof of Concept exploit for it!
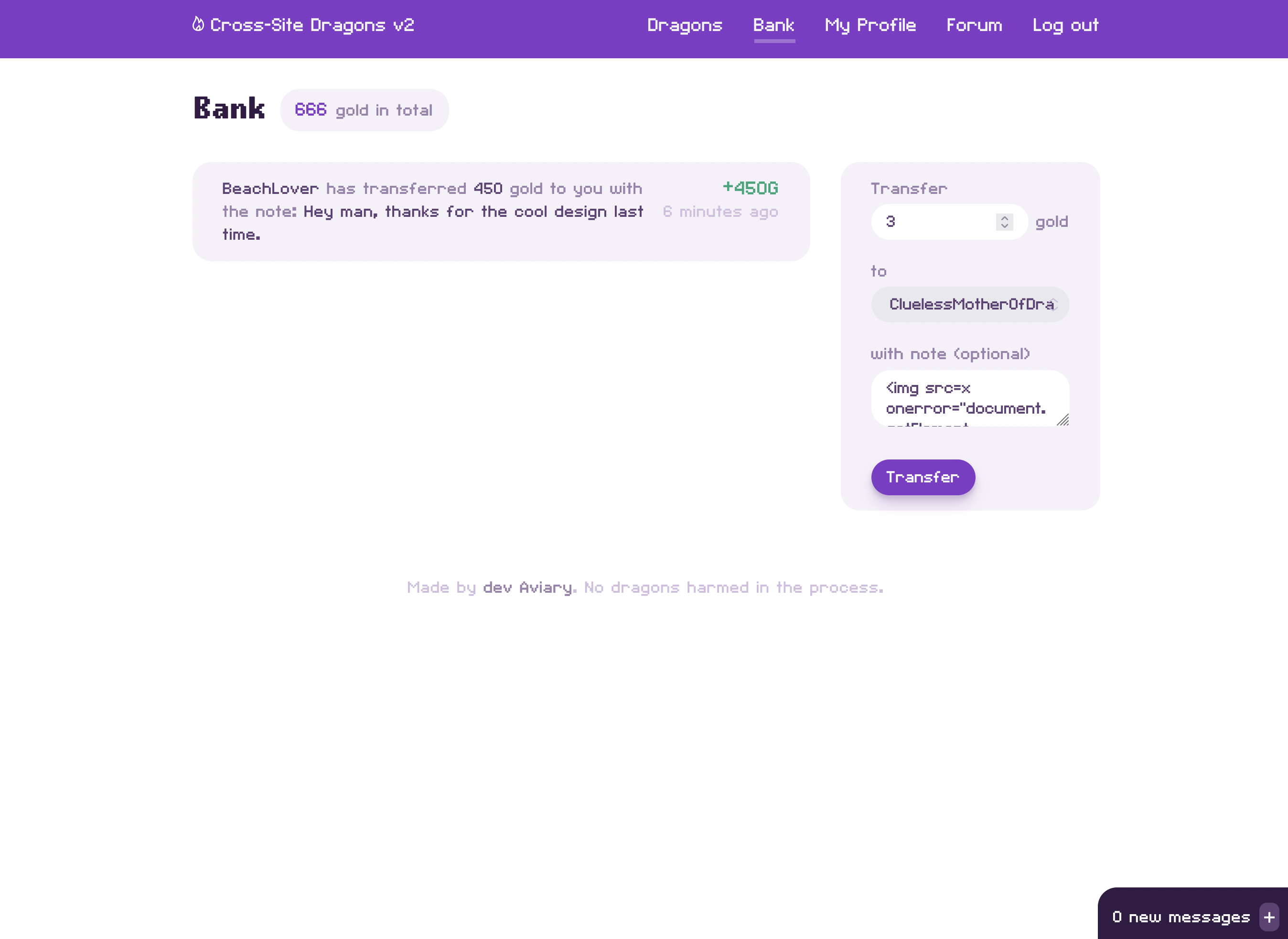
Persistent XSS: Practice
Watch out, the admins of Cross-Site Dragons have finally fixed the vulnerabilities you masterfully exploited back in Reflected XSS: Practice!
But we bet you can find even better vulnerabilities and “convince” some unwitting users’ browsers to transfer some in-game currency to you!
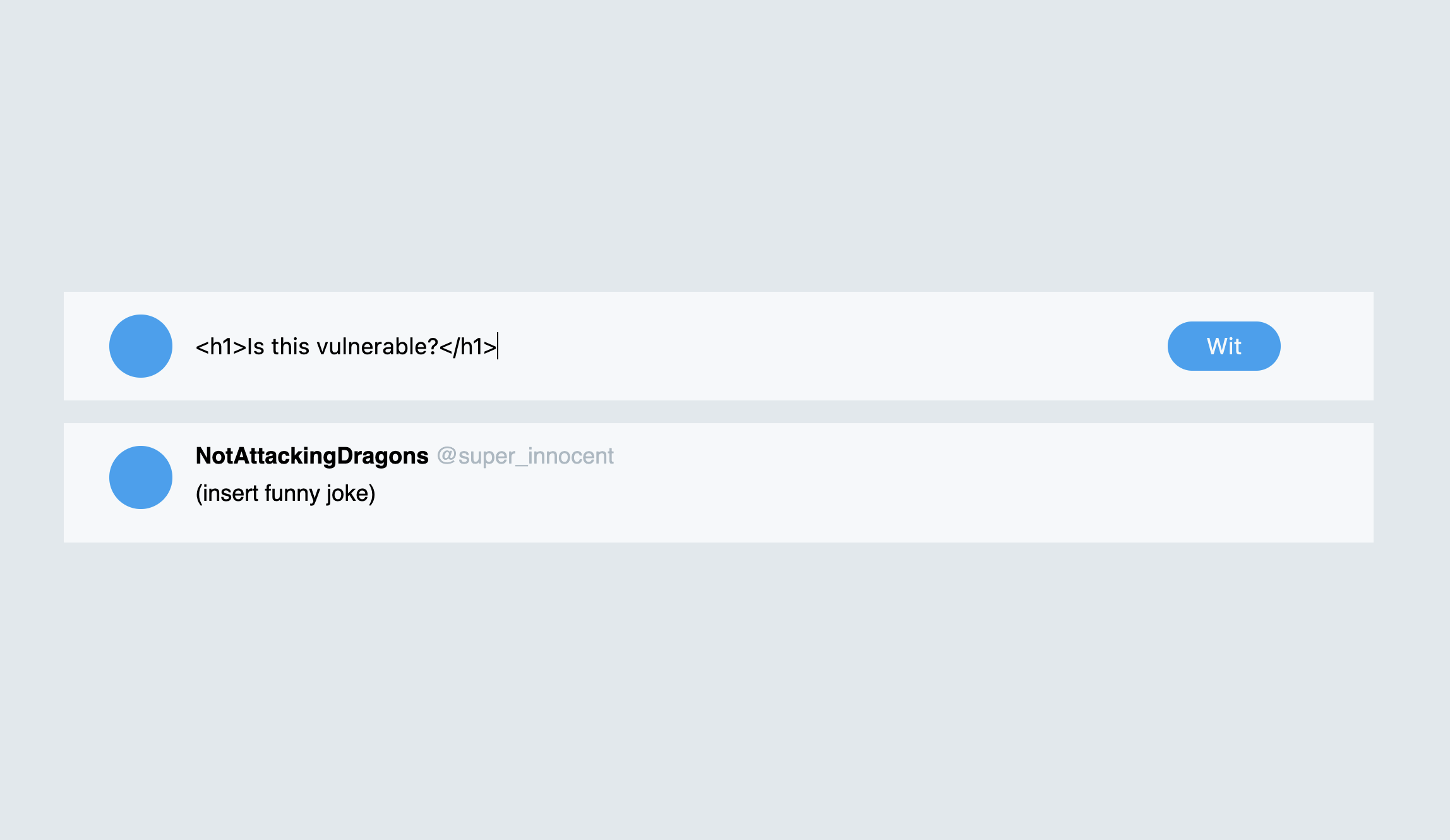
Types of XSS
What is self-XSS? What is DOM-based XSS? Why is the terminology surrounding XSS confusing at times? In this section, we explain all this in concise terms.
How to prevent it
Now that we know how to attack, we learn how to defend: how to encode user input, and how to set secure CSP policies.
Conclusion
Congratulations 🎉 and a recap of this course!
Why we’re worth it

Nina, co-founder
Before you start
- You’ll need some basic HTML & JavaScript knowledge. Plus a general tech background, meaning a little scripting/programming experience and a general understanding of the web.
FAQs.
Kali machineWhat are the specs for my Kali Linux virtual machine?
Internet is disabled, CPU is limited to 1.5 units and RAM is limited to 2G. But other than that, you have access to your machine 24/7.
Will my data (my files, scripts etc) be persisted in my Kali machine?
Store all your scripts & data in ~/nest as this folder (and nothing else!) will be persisted across restarts & updates.
All your servers are too far from me and my machine is laggy. Can you set one up near me?
Of course! Let us know where you’d like your lab to be hosted and we’d happily create a new server near it.
We’re also already working on making servers in the US available.
How long do I get access to the machine?
Subscribers get access for as long as you’re subscribed. If you’ve purchased a course, then you always have access to it.
Can I request additional tools on my machine?
Of course you can! Please contact us with your requests (see our help centre when logged in).
Are there any minimum requirements to run this?
Since there’s an entire machine in our app, make sure your screen is big enough (1920x1680)!
Can I change the location of my machine & labs any time?
Send us your request via the help center when logged in. This will be automated soon!
What’s the refund policy?
We give refunds if requested within 1 month (i.e. for the current month of subscription, or courses purchased less than a month ago).
Are there prerequisites to your courses?
As long as you have a general tech background (programmer, IT, computer science student etc), we don’t assume any prior cybersecurity knowledge!
Why do you require a general tech background for your courses?
Being able to break / exploit something comes from knowing it as well as you know your palm. We leave the prerequisite tech background to other people’s capable hands, so that we can focus on teaching you how to break the tech.