Comprehensive SQL Injection
11 sections
34 challenges
Master SQL injection attacks. Not only will you exploit countless fun SQLI challenges, but by the end of this course, you’ll have written your own automated tools for both SQL and NoSQL languages.
Ready to start?
Ready to start?
Labs
Exploit classic SQLI to redeem games
Catch tax-evading criminals with blind SQLI
Gain an advantage on your exams with NoSQLI
Real software vulns
Breach a Wordpress plugin’s database
Take over someone else’s chat account
Leak the data of a content management system
What’s inside?
Introduction
Before we jump into exciting SQL injection demos and challenges, let’s address some of the most common questions you might have about SQLI!
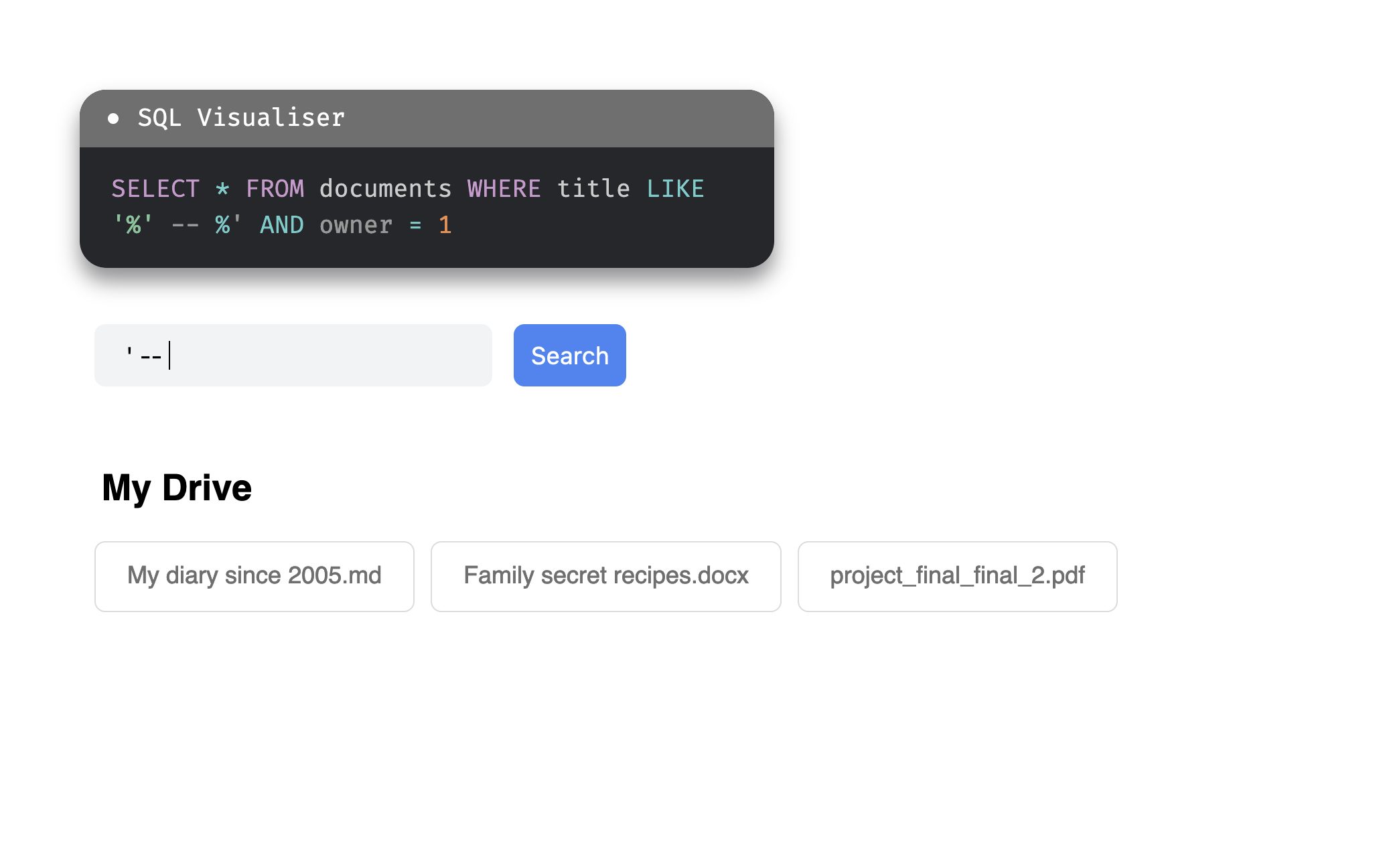
Classic SQLI
We hope you have the next few days off, because we’re booking a
getaway at Hotel Union where you practice SQLIs with the UNION
SELECT technique and steal some credentials!
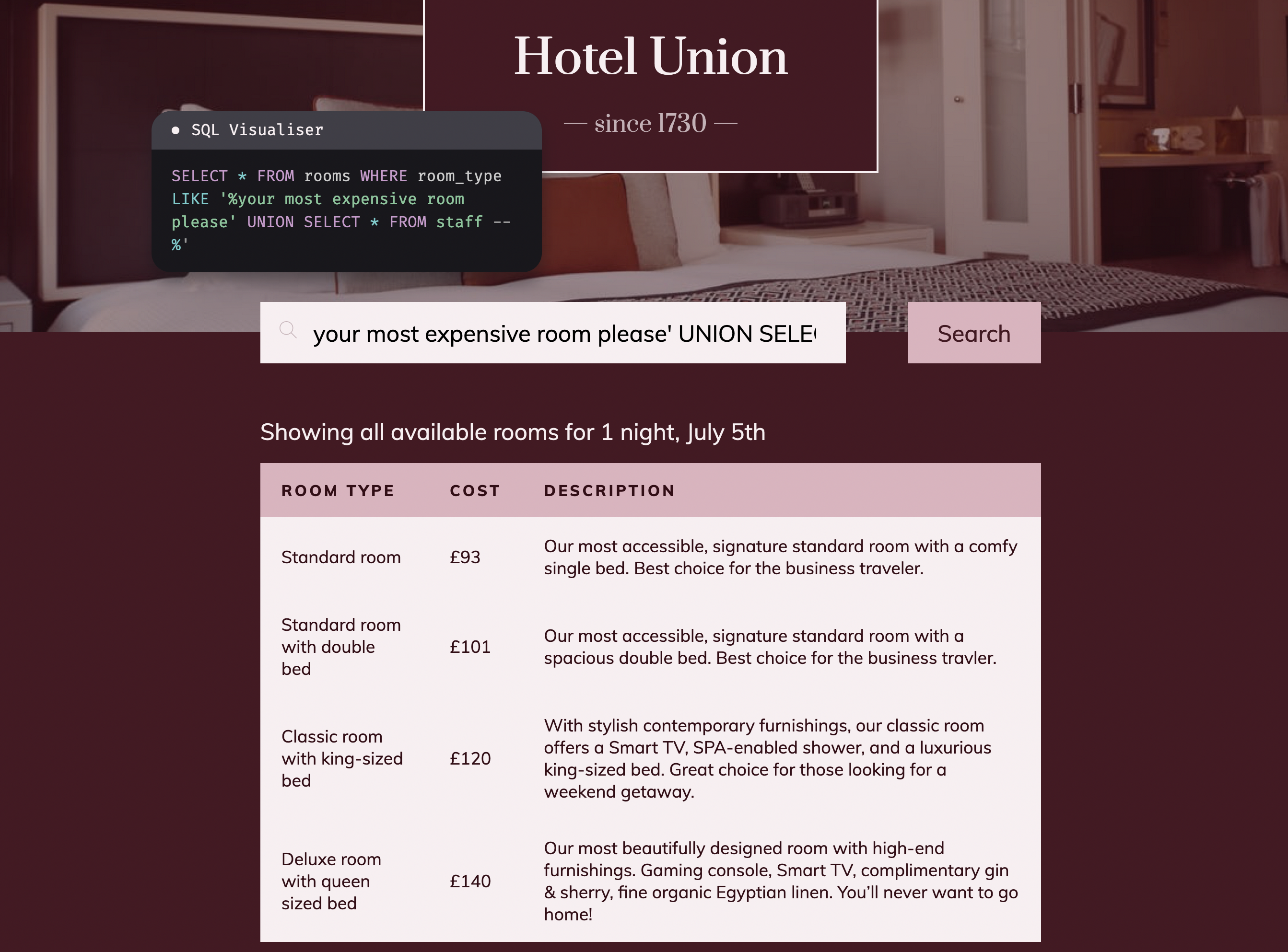
Real world case study: Tutor LMS Plugin UNION-based SQLI
Tutor LMS is a Wordpress plugin for course creation and selling. In versions prior to 1.8.3, the endpoint that returns answers for a given quiz question does not sanitise user input properly nor does it use any parameterised query. This is the perfect condition to practice our UNION-based SQLI attacks in!
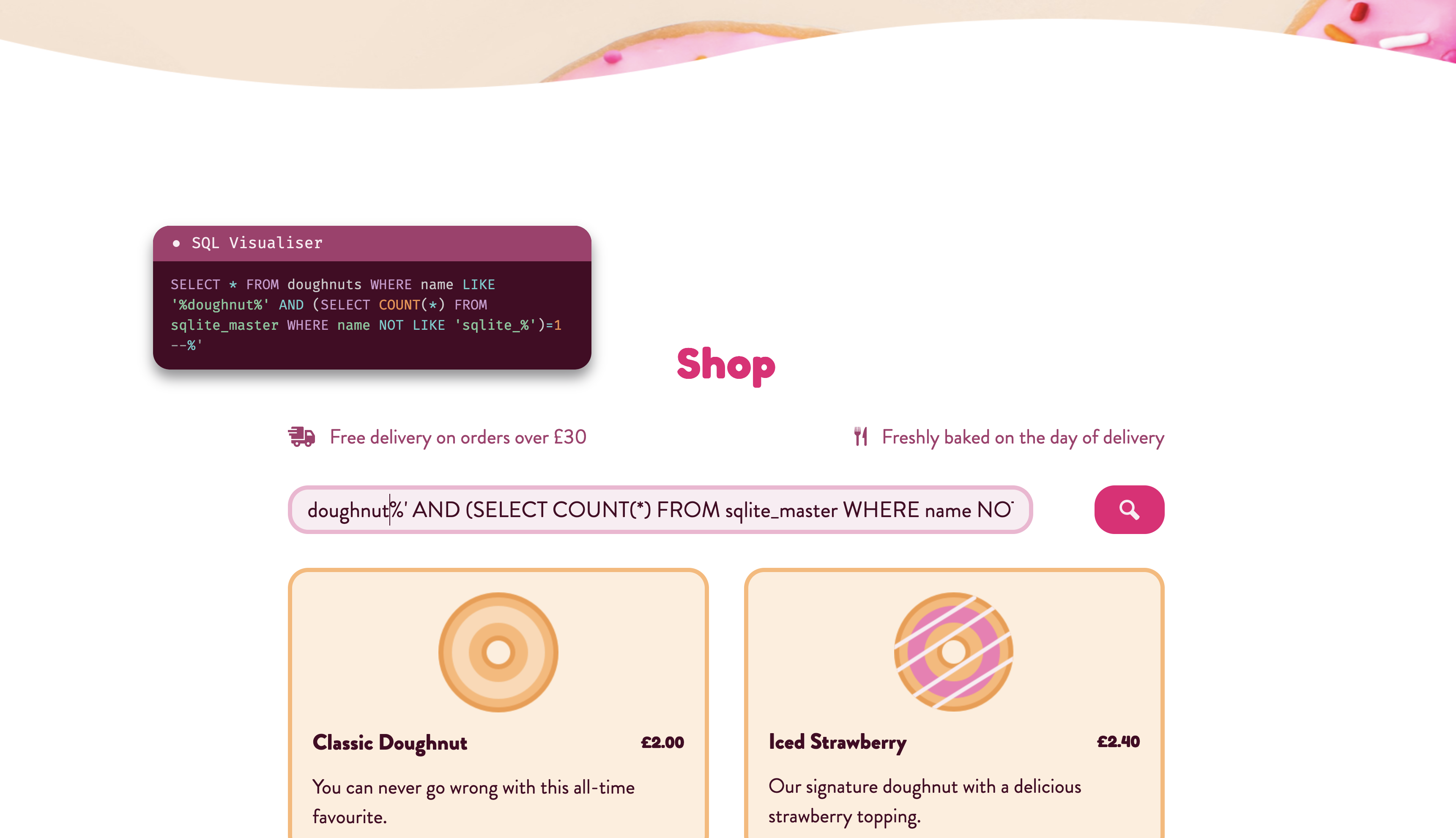
In-Band SQLI Playground: Squeal Games
Squeal Games is a gaming platform where you can buy games, view your achievements, unlock new ones, and chat with your friends. It also conceals two SQLI vulnerabilities that you can exploit to your advantage.
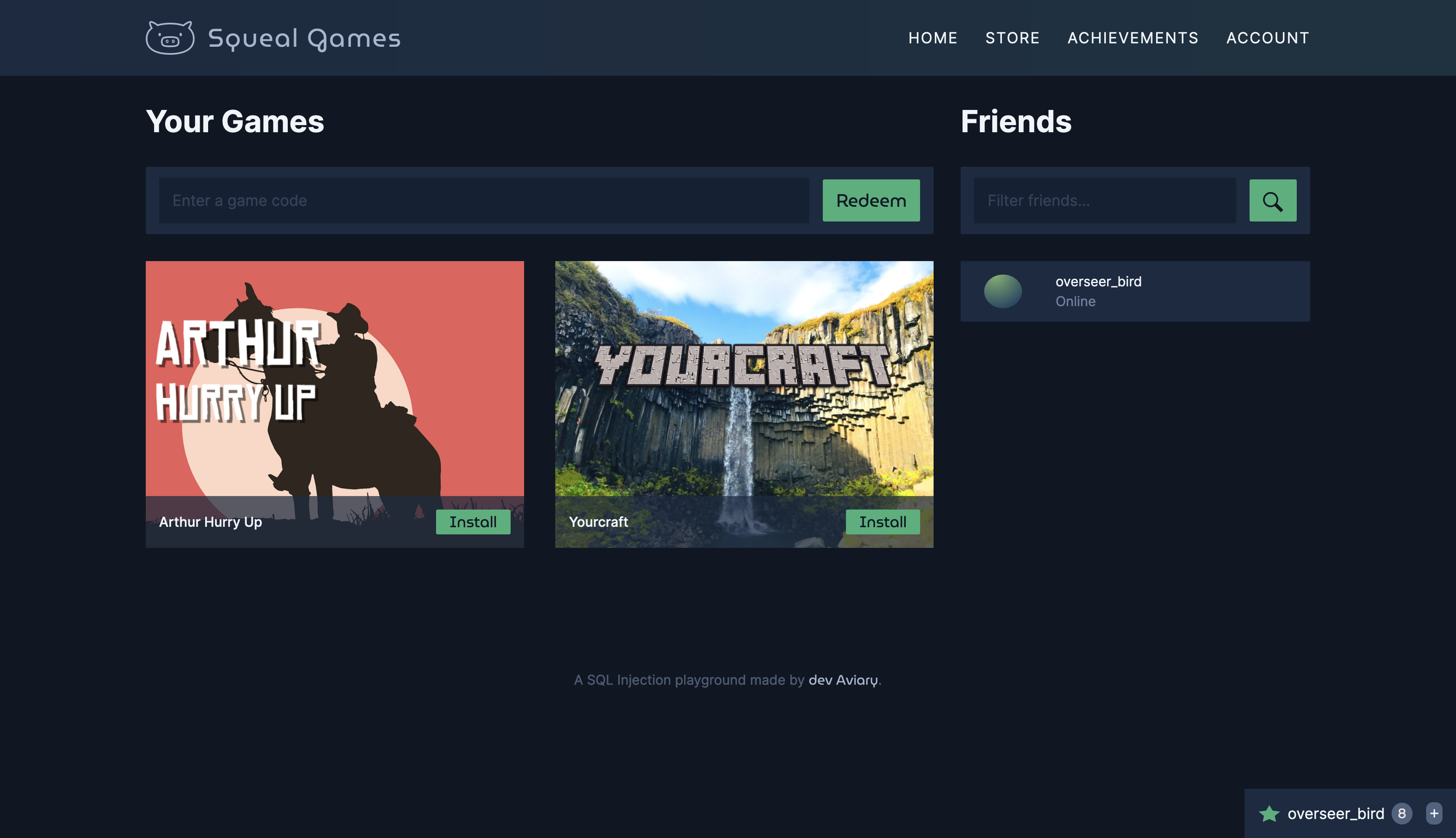
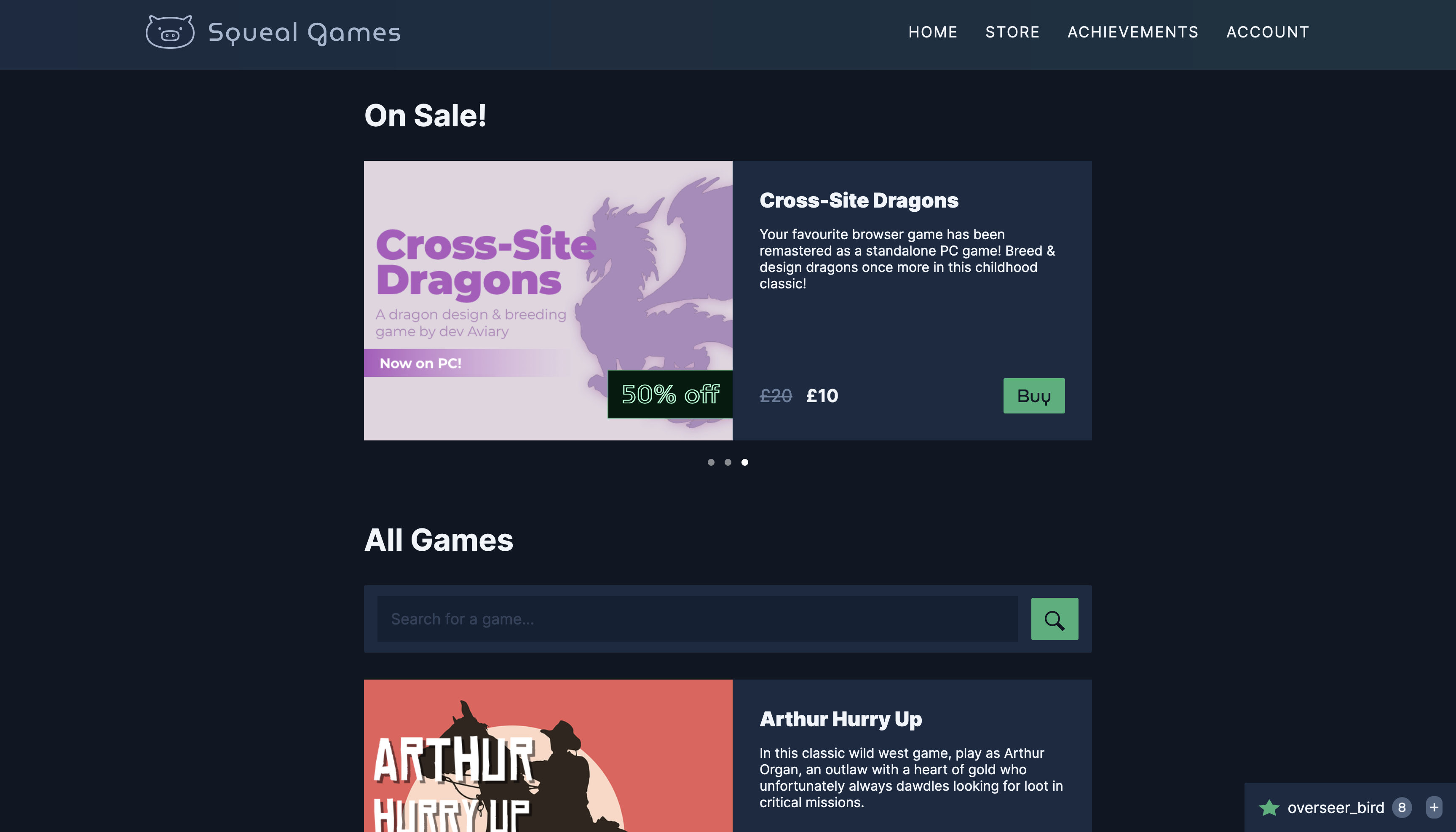
Blind SQLI
It’s easy to exploit a SQLI vulnerability when we can see the SQL
errors directly returned by the app and all the data returned by our
UNION SELECT, but what happens if the developers give
generic errors when they detect a
UNION SELECT?
Strap in, because here you’ll write your own SQLI exploitation tool!
Real world case study: Blind SQLI in Zenario CMS 8.8
We have now covered all the basics of blind SQLI attacks, let’s unleash our skills and our shiny new tools on a real world case study.
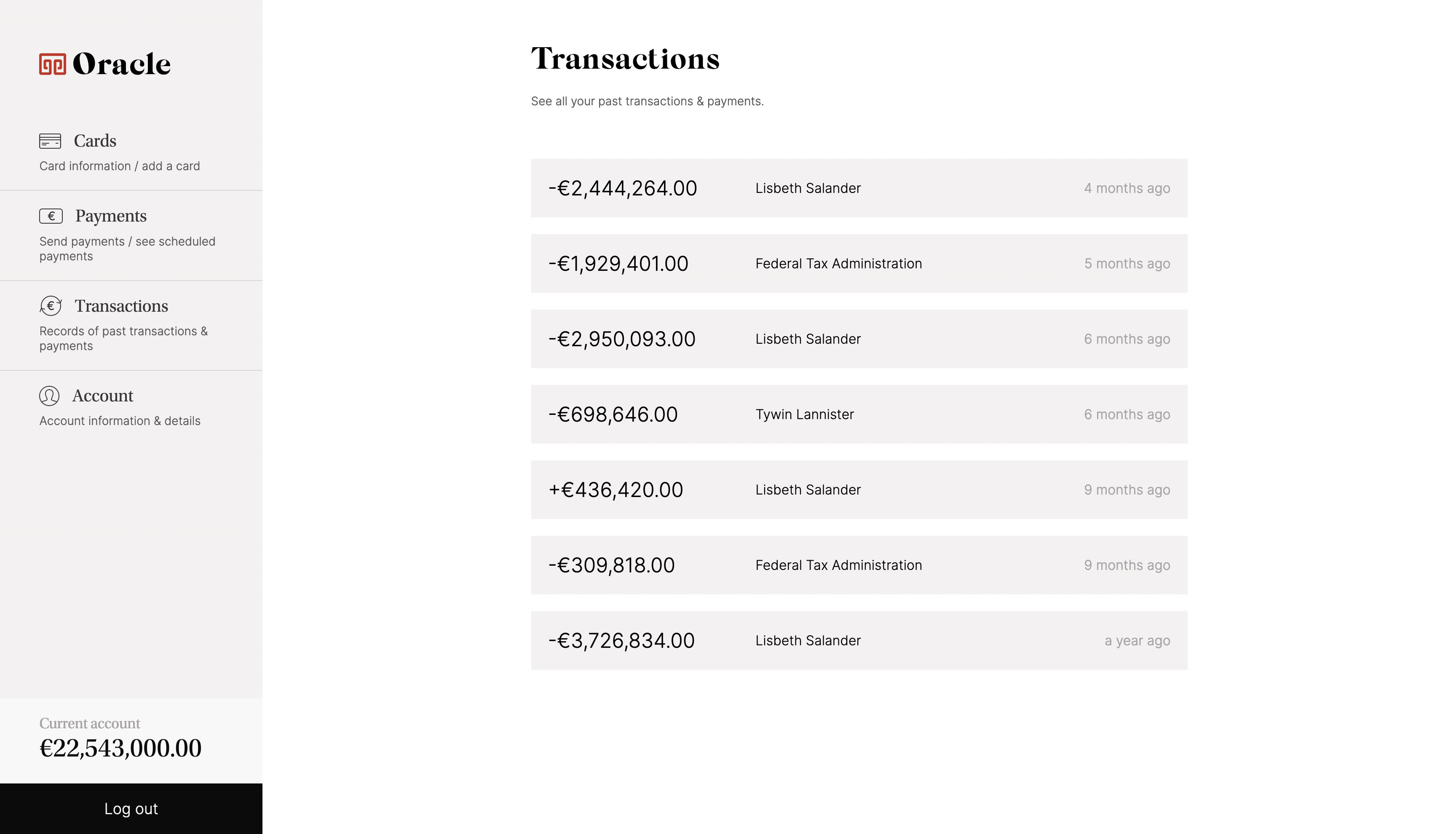
Blind SQLI Playground: Oracle Bank
Instead of exfiltrating data and unlocking passphrases to solve challenges, we are hiring you today to be our consulting detective!
We’re at the end of our ropes trying to catch tax-evading criminals, so we’d like you to look into Oracle Bank using whatever methods you have at your disposal (we’ll turn a blind eye this time).

NoSQLI
What we have in store for you in this section:
- Look at what exactly NoSQL is.
- Get our hands dirty with querying in NoSQL.
- See why NoSQL does not prevent injection attacks.
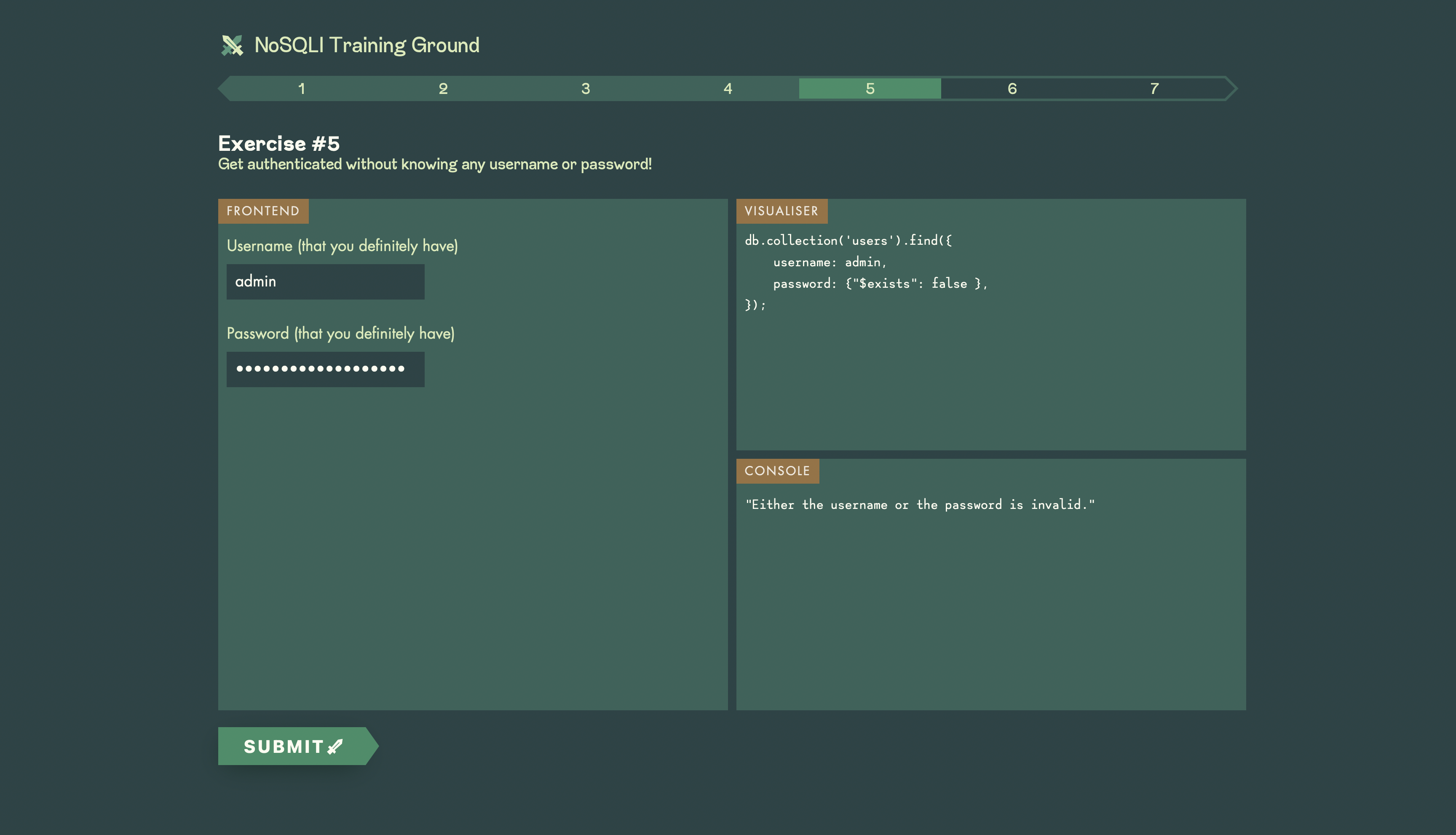
- Practice simple authentication bypass.
- Practice data extraction with blind NoSQLI and error-based NoSQLI.
Case study: Rocket.Chat 3.12.1
Rocket.Chat is an open source web-app for chats, similar to Discord or Slack. On version 3.12.1, if you know the email address of any user, you can take over their account, escalate to admin privileges, and eventually achieve remote code execution (RCE).
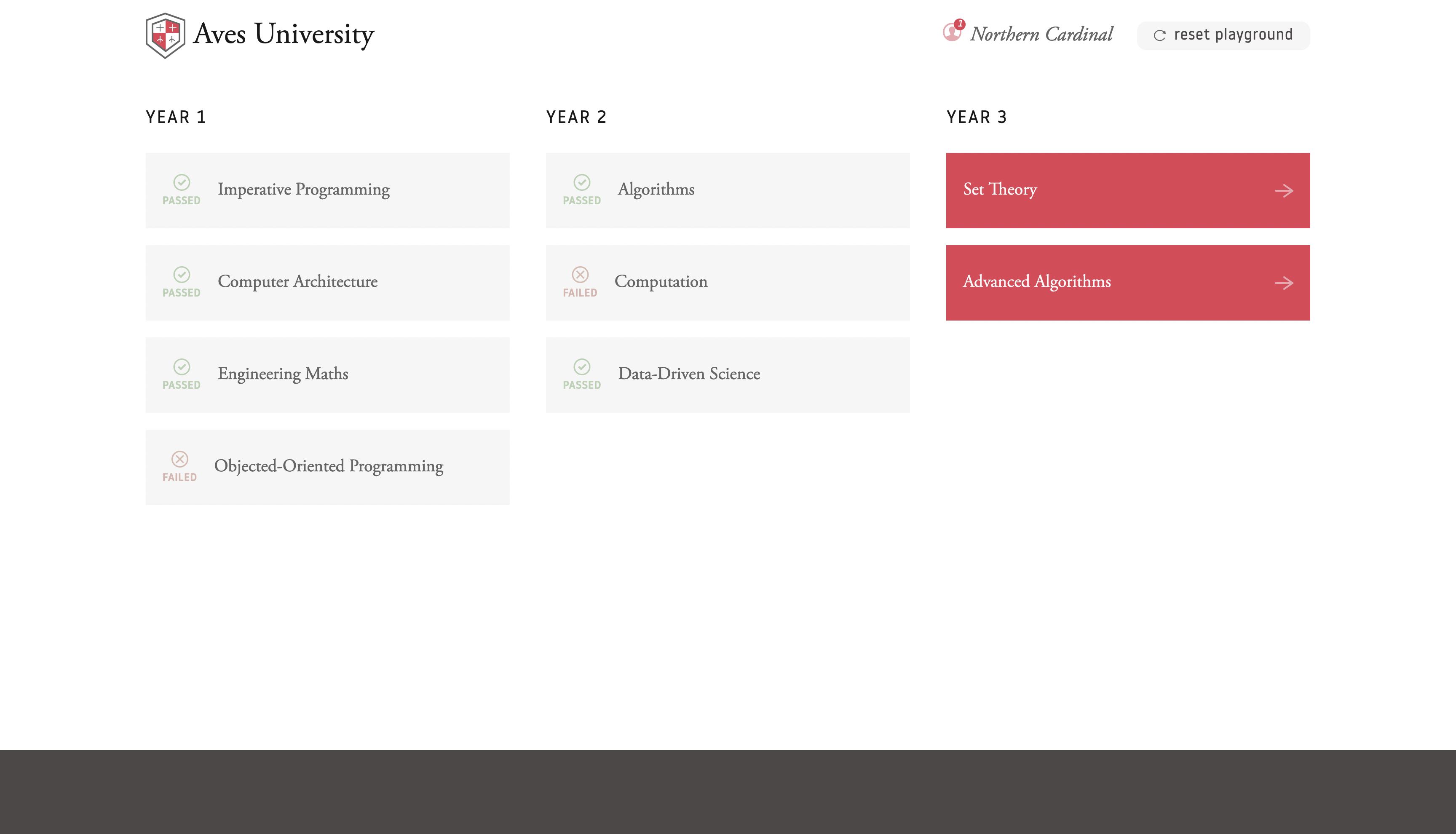
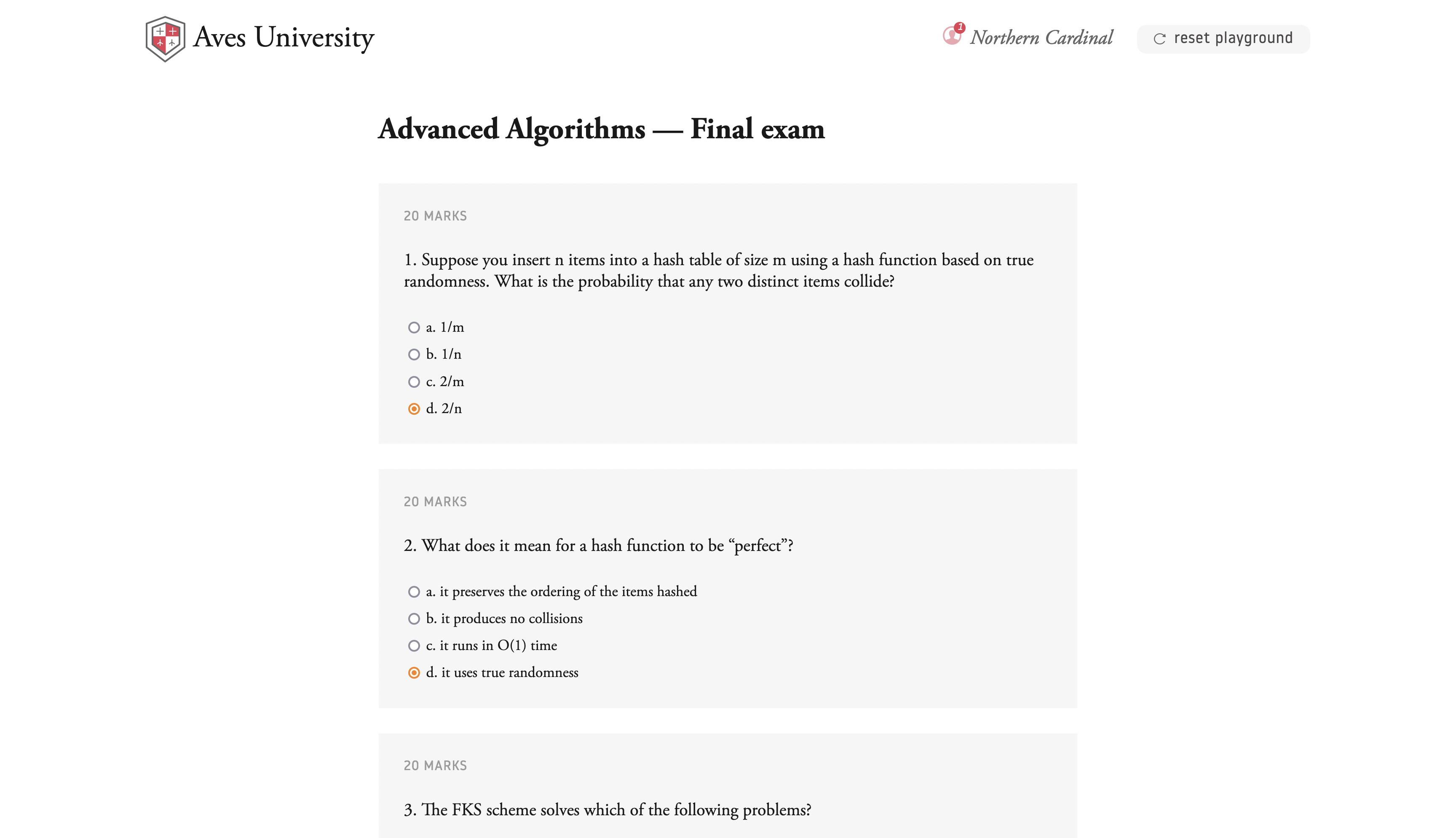
NoSQLI Playground: Aves University
You are an undergraduate student in your final year, ready to graduate. Only... your grades in Advanced Algorithms aren’t as ready as you. You could spend the whole summer resitting those exams, or maybe you could find an easier way to “fix” your grades and graduate on time?
Conclusion
Congratulations 🎉 and a recap of this course!
Why we’re worth it

Nina, co-founder
Prerequisites
- You’ll need some basic SQL knowledge, like how to
SELECT, howWHEREworks, and the concepts of tables (rows & columns). - Plus a general tech background, meaning a little scripting/programming experience and a general understanding of the web.
This course is for you if...
- You want hands-on labs, not just reading or watching videos.
- You like to dive deep, learn the ins and outs of SQLI, and know it in your bones.
- You want to master it completely — enough to write your own exploitation tools.
This course is not for you if...
- You just want the basics of SQLI and work with an automated tool. If so, we recommend you start with sqlmap.
FAQs.
Kali machineWhat are the specs for my Kali Linux virtual machine?
Internet is disabled, CPU is limited to 1.5 units and RAM is limited to 2G. But other than that, you have access to your machine 24/7.
Will my data (my files, scripts etc) be persisted in my Kali machine?
Store all your scripts & data in ~/nest as this folder (and nothing else!) will be persisted across restarts & updates.
All your servers are too far from me and my machine is laggy. Can you set one up near me?
Of course! Let us know where you’d like your lab to be hosted and we’d happily create a new server near it.
We’re also already working on making servers in the US available.
How long do I get access to the machine?
Subscribers get access for as long as you’re subscribed. If you’ve purchased a course, then you always have access to it.
Can I request additional tools on my machine?
Of course you can! Please contact us with your requests (see our help centre when logged in).
Are there any minimum requirements to run this?
Since there’s an entire machine in our app, make sure your screen is big enough (1920x1680)!
Can I change the location of my machine & labs any time?
Send us your request via the help center when logged in. This will be automated soon!
What’s the refund policy?
We give refunds if requested within 1 month (i.e. for the current month of subscription, or courses purchased less than a month ago).
Are there prerequisites to your courses?
As long as you have a general tech background (programmer, IT, computer science student etc), we don’t assume any prior cybersecurity knowledge!
Why do you require a general tech background for your courses?
Being able to break / exploit something comes from knowing it as well as you know your palm. We leave the prerequisite tech background to other people’s capable hands, so that we can focus on teaching you how to break the tech.